Thursday, 28 July 2016
How To Hack Any Wifi Network Password Using Cmd
step one
Go to command prompt, click start up menu on your system, click RUN, type Cmd, and click ok to open the command prompt
step two
inside the command prompt, type the following
netsh wlan show networks
mode = bssid(it will show all the available wifi network, take note of the names)
step 3
To connect to the wifi network, type the following
netsh wlan connect
name= (put the name of wifi your system detect)
e.g net wlan connect
name = (kinibigdeal pc)
step 4
press enter to connect
step 5
To disconnect it, type
netsh wlan disconnect
step 6
To save it type : netsh wlan export profile name = kinibigdeal( not by name but change it to the name of the detected wifi)
How to Hack any wifi Network Password by using Cmd:
Sometimes you might be frustrated especially when your system detect a wifi network but you are restricted from accessing it due to users password, now i can teach you a simple trick to hack the password.
step one
Go to command prompt, click start up menu on your system, click RUN, type Cmd, and click ok to open the command prompt
step two
inside the command prompt, type the following
netsh wlan show networks
mode = bssid(it will show all the available wifi network, take note of the names)
step 3
To connect to the wifi network, type the following
netsh wlan connect
name= (put the name of wifi your system detect)
e.g net wlan connect
name = (kinibigdeal pc)
step 4
press enter to connect
step 5
To disconnect it, type
netsh wlan disconnect
step 6
To save it type : netsh wlan export profile name = kinibigdeal( not by name but change it to the name of the detected wifi)
What is the difference between RIP, IGRP and EIGRP?
Wednesday, 27 July 2016
Difference Between WCDMA and GSM
1.WCDMA is a 3G technology while GSM is a 2G technology
2.GSM is slowly being phased out in favor of CDMA
3.GSM is still more widespread than CDMA
4.WCDMA and GSM uses different frequency bands
5.WCDMA offers much faster data speeds than GSM
6.WCDMA would soon replace GSM
FDM vs. TDM
Sunday, 24 July 2016
IPTV (Internet Protocol television)
and high-speed Internet access.
Saturday, 23 July 2016
Friday, 22 July 2016
Difference between hub and switch
Difference between hub and switch
Network Hub
Network Switch
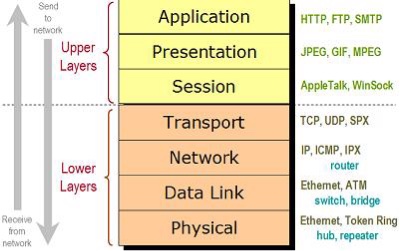
OSI Model layers

Thursday, 21 July 2016
Router vs Switch vs Hub: The Devices Defined
Router vs Switch vs Hub: The Devices Defined
What is a Switch?
Finally, what is a Hub?
The Differences Between a
Router, Switch and Hub on the Network
Hub vs Switch: Similar
Roles
In a hub, a frame is passed along or "broadcast" to every one of its ports. It doesn't matter that the frame is only destined for one port. The hub has no way of distinguishing which port a frame should be sent to. Passing it along to every port ensures that it will reach its intended destination. This places a lot of traffic on the network and can lead to poor network response times.
Additionally, a 10/100Mbps hub must share its bandwidth with each and every one of its ports. So when only one PC is broadcasting, it will have access to the maximum available bandwidth. If, however, multiple PCs are broadcasting, then that bandwidth will need to be divided among all of those systems, which will degrade performance.
A switch, however, keeps a record of the MAC addresses of all the devices connected to it. With this information, a switch can identify which system is sitting on which port. So when a frame is received, it knows exactly which port to send it to, without significantly increasing network response times. And, unlike a hub, a 10/100Mbps switch will allocate a full 10/100Mbps to each of its ports. So regardless of the number of PCs transmitting, users will always have access to the maximum amount of bandwidth. It's for these reasons a switch is considered to be a much better choice than a hub.
Routers are Completely
Different Devices
A router is typically connected to at least two networks, commonly two Local Area Networks (LANs) or Wide Area Networks (WAN) or a LAN and its ISP's network . for example, your PC or workgroup and EarthLink. Routers are located at gateways, the places where two or more networks connect. Using headers and forwarding tables, routers determine the best path for forwarding the packets. Router use protocols such as ICMP to communicate with each other and configure the best route between any two hosts.
Features of Integrated
Routers
All routers have a WAN Port that connects to a DSL or cable modem for broadband Internet service and the integrated switch allows users to easily create a LAN. This allows all the PCs on the LAN to have access to the Internet and Windows file and printer sharing services.
Some of the more high-end or business class routers will also incorporate a serial port that can be connected to an external dial-up modem, which is useful as a backup in the event that the primary broadband connection goes down, as well as a built in LAN printer server and printer port.
Besides the inherent protection features provided by the NAT, many routers will also have a built-in, configurable, hardware-based firewall. Firewall capabilities can range from the very basic to quite sophisticated devices. Among the capabilities found on leading routers are those that permit configuring TCP/UDP ports for games, chat services, and the like, on the LAN behind the firewall.
So, in short, a hub glues together an Ethernet network segment, a switch can connect multiple Ethernet segments more efficiently and a router can do those functions plus route TCP/IP packets between multiple LANs and/or WANs; and much more of course.
Wednesday, 20 July 2016
5G technology
5G is the coming fifth-generation wireless broadband technology based on the IEEE 802.11ac standard.
5G will provide better speeds and coverage than the current 4G. 5G operates with a 5Ghz signal and is set to offer speeds of up to 1 Gb/s for tens of connections or tens of Mb/s for tens of thousands of connections. Huawei, a major player in the Chinese mobile market, believes 5G will provide speeds 100x faster than 4G LTE offers. 5G also increases network expandability up to hundreds of thousands of connections.
The signal technology of 5G has also been improved for greater coverage as well as spectral and signaling efficiency. These improvements stand to further enable changes like pervasive computing and the Internet of Things (IoT).
Although 5G is not scheduled for launch until 2020, some manufacturers are already incorporating elements of the coming standard's specifications into their
Products.

Network topology
Network Topology
Point-to-Point
Bus
Star
Ring
Mesh
Monday, 18 July 2016
Difference between Data and information
Main difference:
Data VS Information
Data:
Information:
Tuesday, 12 July 2016
CCNA commands and explanation
- sho running-config- To
verify loopback address
- sho ip ospf database-
Verifies the new RID of each router
- sho ip ospf interface-
Verifies the new RID of each router










